8.8 无线局域网的安全#
8.8 Securing Wireless LANs
在无线网络中,安全性尤为重要,因为携带帧的无线电波可以传播得远远超过包含无线基站和主机的建筑物。本节将简要介绍无线安全。欲了解更深入的内容,请参见 Edney 和 Arbaugh 撰写的易读书籍 [Edney 2003]。
802.11 中的安全问题在技术界和媒体中都引起了相当大的关注。虽然讨论颇多,但争论甚少——似乎普遍认同原始 802.11 规范存在许多严重的安全漏洞。事实上,现在可以下载到公开的软件利用这些漏洞,使得使用原始 802.11 安全机制的用户面临的安全攻击风险与不使用任何安全功能的用户一样大。
以下章节中,我们将讨论最初在 802.11 规范中标准化的安全机制,统称为 有线等效保密(Wired Equivalent Privacy, WEP)。顾名思义,WEP 旨在提供与有线网络相似的安全级别。随后我们将讨论 WEP 中的一些安全漏洞,并介绍 2004 年采用的更安全的 802.11i 标准。
Security is a particularly important concern in wireless networks, where radio waves carrying frames can propagate far beyond the building containing the wireless base station and hosts. In this section we present a brief introduction to wireless security. For a more in-depth treatment, see the highly readable book by Edney and Arbaugh [Edney 2003].
The issue of security in 802.11 has attracted considerable attention in both technical circles and in the media. While there has been considerable discussion, there has been little debate—there seems to be universal agreement that the original 802.11 specification contains a number of serious security flaws. Indeed, public domain software can now be downloaded that exploits these holes, making those who use the vanilla 802.11 security mechanisms as open to security attacks as users who use no security features at all.
In the following section, we discuss the security mechanisms initially standardized in the 802.11 specification, known collectively as Wired Equivalent Privacy (WEP). As the name suggests, WEP is meant to provide a level of security similar to that found in wired networks. We’ll then discuss a few of the security holes in WEP and discuss the 802.11i standard, a fundamentally more secure version of 802.11 adopted in 2004.
8.8.1 有线等效保密 (WEP)#
8.8.1 Wired Equivalent Privacy (WEP)
IEEE 802.11 WEP 协议设计于 1999 年,采用对称共享密钥方法,在主机与无线接入点(即基站)之间提供认证和数据加密。WEP 未指定密钥管理算法,因此假设主机与无线接入点通过带外方法已达成密钥共识。认证过程如下:
无线主机向接入点请求认证。
接入点响应认证请求,发送一个 128 字节的随机数(nonce)。
无线主机使用与接入点共享的对称密钥加密该随机数。
接入点解密主机加密的随机数。
若解密出的随机数与最初发送给主机的随机数匹配,则接入点认证通过该主机。
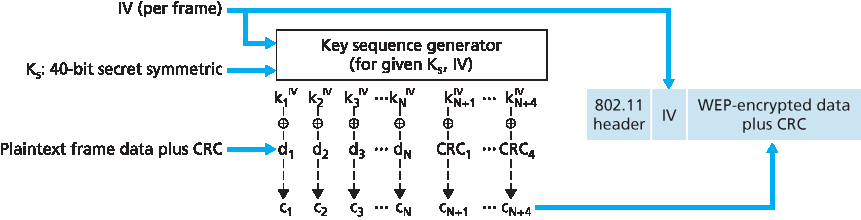
图 8.30 802.11 WEP 协议
WEP 数据加密算法如 图 8.30 所示。假设主机和接入点均知晓一个秘密的 40 位对称密钥 KS。另有一个 24 位初始化向量(IV)附加在 40 位密钥后,构成 64 位密钥,用于加密单帧。IV 会随帧变化,因此每帧使用不同的 64 位密钥。加密过程如下。首先计算数据负载的 4 字节 CRC 值(参见 第 6.2 节)。然后使用 RC4 流密码对负载和这 4 字节 CRC 进行加密。这里不详细介绍 RC4(详见 [Schneier 1995] 和 [Edney 2003])。我们只需知道,给定一个密钥值(本例中为 64 位(KS, IV)密钥),RC4 算法会生成一串密钥流 k1IV,k2IV,k3IV,…,用于对帧内的数据和 CRC 进行加密。实际操作中,可按字节处理。加密通过将数据的第 i 个字节 di 与密钥流的第 i 个字节 kiIV 异或产生密文第 i 字节 ci:
ci = di ⊕ kiIV
IV 在帧间变化,并以明文形式包含在每个 WEP 加密 802.11 帧的头部,如 图 8.30 所示。接收方使用与发送方共享的 40 位对称密钥,加上该 IV,构造出与发送方相同的 64 位密钥用以解密:
di = ci ⊕ kiIV
RC4 算法的正确使用要求相同的 64 位密钥值绝不重复使用。回想 WEP 密钥在帧间变化。对于给定的 KS(很少变动),只有 2^24 个唯一密钥。如果这些密钥随机选取,[Edney 2003] 证明在仅传输 12,000 帧后,出现重复 IV(即重复 64 位密钥)的概率超过 99%。以 1KB 帧大小和 11 Mbps 传输速率,仅需几秒即可传输 12,000 帧。此外,由于 IV 以明文形式在帧中传输,窃听者一旦发现重复 IV,即知道密钥被重复使用。
为说明使用重复密钥时出现的问题,考虑 Trudy 针对 Alice 发起的选择明文攻击。假设 Trudy(可能通过 IP 欺骗)发送请求(如 HTTP 或 FTP 请求)给 Alice,要求发送内容已知的数据 d1, d2, d3, d4,…。Trudy 还观察到加密后的数据 c1, c2, c3, c4,…。由于 di = ci ⊕ kiIV,Trudy 对等式两边 XOR ci 得:
di ⊕ ci = kiIV
有了此关系,Trudy 可以用已知的 di 和 ci 计算出 kiIV。下次当 Trudy 看到相同 IV 被使用时,即知道密钥序列 k1IV, k2IV, k3IV,…,从而能解密加密消息。
WEP 还有其他安全隐患。[Fluhrer 2001] 描述了利用 RC4 某些弱密钥的攻击方法。[Stubblefield 2002] 讨论了有效实现和利用此攻击的方式。另一个关注点是 图 8.30 中显示并在 802.11 帧中传输的 CRC 位,用于检测负载中被篡改的位。然而,攻击者可更改加密内容(如用乱码替换原始加密数据),计算替换乱码的 CRC,并将其放入 WEP 帧,生成一个接收方可接受的 802.11 帧。对此,需要使用我们在 第 8.3 节 学习过的消息完整性技术来检测内容篡改或替换。有关 WEP 安全性的更多细节,请参见 [Edney 2003; Wright 2015] 及其中参考文献。
The IEEE 802.11 WEP protocol was designed in 1999 to provide authentication and data encryption between a host and a wireless access point (that is, base station) using a symmetric shared key approach. WEP does not specify a key management algorithm, so it is assumed that the host and wireless access point have somehow agreed on the key via an out-of-band method. Authentication is carried out as follows:
A wireless host requests authentication by an access point.
The access point responds to the authentication request with a 128-byte nonce value.
The wireless host encrypts the nonce using the symmetric key that it shares with the access point.
The access point decrypts the host-encrypted nonce.
If the decrypted nonce matches the nonce value originally sent to the host, then the host is authenticated by the access point.

Figure 8.30 802.11 WEP protocol
The WEP data encryption algorithm is illustrated in Figure 8.30. A secret 40-bit symmetric key, KS, is assumed to be known by both a host and the access point. In addition, a 24-bit Initialization Vector (IV) is appended to the 40-bit key to create a 64-bit key that will be used to encrypt a single frame. The IV will change from one frame to another, and hence each frame will be encrypted with a different 64-bit key. Encryption is performed as follows. First a 4-byte CRC value (see Section 6.2) is computed for the data payload. The payload and the four CRC bytes are then encrypted using the RC4 stream cipher. We will not cover the details of RC4 here (see [Schneier 1995] and [Edney 2003] for details). For our purposes, it is enough to know that when presented with a key value (in this case, the 64-bit (KS, IV) key), the RC4 algorithm produces a stream of key values, k1IV,k2IV,k3IV,… that are used to encrypt the data and CRC value in a frame. For practical purposes, we can think of these operations being performed a byte at a time. Encryption is performed by XOR-ing the ith byte of data, di, with the ith key, kiIV, in the stream of key values generated by the (KS, IV) pair to produce the ith byte of ciphertext, ci:
ci=di⊕kiIV
The IV value changes from one frame to the next and is included in plaintext in the header of each WEP-encrypted 802.11 frame, as shown in Figure 8.30. The receiver takes the secret 40-bit symmetric key that it shares with the sender, appends the IV, and uses the resulting 64-bit key (which is identical to the key used by the sender to perform encryption) to decrypt the frame:
di=ci⊕kiIV
Proper use of the RC4 algorithm requires that the same 64-bit key value never be used more than once. Recall that the WEP key changes on a frame-by-frame basis. For a given KS (which changes rarely, if ever), this means that there are only 224 unique keys. If these keys are chosen randomly, we can show [Edney 2003] that the probability of having chosen the same IV value (and hence used the same 64-bit key) is more than 99 percent after only 12,000 frames. With 1 Kbyte frame sizes and a data transmission rate of 11 Mbps, only a few seconds are needed before 12,000 frames are transmitted. Furthermore, since the IV is transmitted in plaintext in the frame, an eavesdropper will know whenever a duplicate IV value is used.
To see one of the several problems that occur when a duplicate key is used, consider the following chosen-plaintext attack taken by Trudy against Alice. Suppose that Trudy (possibly using IP spoofing) sends a request (for example, an HTTP or FTP request) to Alice to transmit a file with known content, d1, d2, d3, d4,…. Trudy also observes the encrypted data c1, c2, c3, c4,…. Since di=ci⊕kiIV, if we XOR ci with each side of this equality we have
di⊕ci=kiIV
With this relationship, Trudy can use the known values of di and ci to compute kiIV. The next time Trudy sees the same value of IV being used, she will know the key sequence k1IV,k2IV,k3IV,… and will thus be able to decrypt the encrypted message.
There are several additional security concerns with WEP as well. [Fluhrer 2001] described an attack exploiting a known weakness in RC4 when certain weak keys are chosen. [Stubblefield 2002] discusses efficient ways to implement and exploit this attack. Another concern with WEP involves the CRC bits shown in Figure 8.30 and transmitted in the 802.11 frame to detect altered bits in the payload. However, an attacker who changes the encrypted content (e.g., substituting gibberish for the original encrypted data), computes a CRC over the substituted gibberish, and places the CRC into a WEP frame can produce an 802.11 frame that will be accepted by the receiver. What is needed here are message integrity techniques such as those we studied in Section 8.3 to detect content tampering or substitution. For more details of WEP security, see [Edney 2003; Wright 2015] and the references therein.
8.8.2 IEEE 802.11i#
在 IEEE 802.11 于 1999 年发布后不久,便开始开发一个具有更强安全机制的新版 802.11。该新标准被称为 802.11i,并于 2004 年完成最终批准。正如我们将看到的,虽然 WEP 提供了相对较弱的加密、仅有单一的认证方式且没有密钥分发机制,IEEE 802.11i 则提供了更强的加密形式、一套可扩展的认证机制以及密钥分发机制。下面我们介绍 802.11i 的概览;一份优秀的(流式音频)802.11i 技术概览见 [TechOnline 2012]。
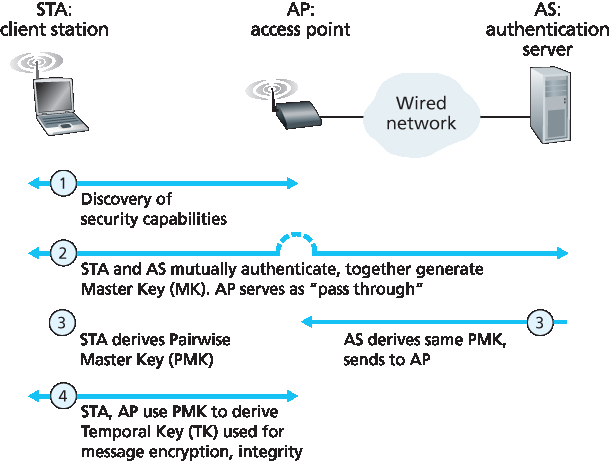
图 8.31 802.11i:四个操作阶段
图 8.31 概述了 802.11i 框架。除了无线客户端和接入点,802.11i 还定义了一个认证服务器,接入点可与其通信。将认证服务器与接入点分离,使一个认证服务器能够服务多个接入点,实现认证和访问决策的集中管理(这些决策通常比较敏感),并保持接入点的成本和复杂性较低。802.11i 分四个阶段运行:
发现阶段。在发现阶段,接入点广播其存在及可向无线客户端节点提供的认证和加密形式。客户端随后请求其期望的具体认证和加密方式。尽管客户端和接入点已开始消息交换,但客户端尚未认证且无加密密钥,因此在客户端能够通过无线通道与任意远程主机通信之前,还需经过若干步骤。
相互认证与主密钥(MK)生成。认证发生在无线客户端与认证服务器之间。此阶段中,接入点主要作为中继,转发客户端和认证服务器之间的消息。 可扩展认证协议(EAP) [RFC 3748] 定义了客户端与认证服务器间简单请求/响应模式的端到端消息格式。如 图 8.32 所示,EAP 消息通过 EAPoL (局域网上的 EAP,参见 [IEEE 802.1X])封装,并在 802.11 无线链路上传输。这些 EAP 消息在接入点被解封装后,再用 RADIUS 协议封装,通过 UDP/IP 传送至认证服务器。虽然 802.11i 协议不强制使用 RADIUS 服务器和协议 [RFC 2865],但它们是 802.11i 的事实标准组件。近期标准化的 DIAMETER 协议 [RFC 3588] 预计将很快替代 RADIUS。
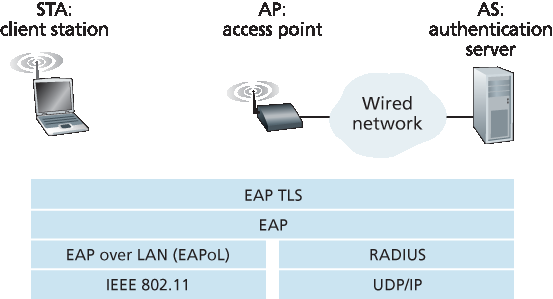
图 8.32 EAP 是一个端到端协议。EAP 消息通过无线链路在客户端和接入点间使用 EAPoL 封装,在接入点与认证服务器间通过 UDP/IP 使用 RADIUS 封装
通过 EAP,认证服务器可以选择多种认证方式之一。尽管 802.11i 并不强制某种认证方法,EAP-TLS 认证方案 [RFC 5216] 被广泛采用。EAP-TLS 使用类似于我们在 第 8.3 节 学习的公钥技术(包括随机数加密和消息摘要),允许客户端与认证服务器相互认证,并推导出双方共有的主密钥(MK)。
成对主密钥(PMK)生成。MK 是客户端和认证服务器共享的秘密,用于生成第二个密钥——成对主密钥(PMK)。认证服务器随后将 PMK 发送给接入点。至此,我们达到了目标!客户端和接入点现拥有共享密钥(回想 WEP 时,密钥分发问题根本未解决),且已相互认证,准备开始正常通信。
临时密钥(TK)生成。利用 PMK,无线客户端和接入点现在可以生成用于通信的附加密钥。其中尤其重要的是临时密钥(TK),它将用于对无线链路上传输到任意远程主机的数据进行链路层加密。
802.11i 提供了多种加密形式,包括基于 AES 的加密方案和增强版 WEP 加密。
Soon after the 1999 release of IEEE 802.11, work began on developing a new and improved version of 802.11 with stronger security mechanisms. The new standard, known as 802.11i, underwent final ratification in 2004. As we’ll see, while WEP provided relatively weak encryption, only a single way to perform authentication, and no key distribution mechanisms, IEEE 802.11i provides for much stronger forms of encryption, an extensible set of authentication mechanisms, and a key distribution mechanism. In the following, we present an overview of 802.11i; an excellent (streaming audio) technical overview of 802.11i is [TechOnline 2012].

Figure 8.31 802.11i: Four phases of operation
Figure 8.31 overviews the 802.11i framework. In addition to the wireless client and access point, 802.11i defines an authentication server with which the AP can communicate. Separating the authentication server from the AP allows one authentication server to serve many APs, centralizing the (often sensitive) decisions regarding authentication and access within the single server, and keeping AP costs and complexity low. 802.11i operates in four phases:
Discovery. In the discovery phase, the AP advertises its presence and the forms of authentication and encryption that can be provided to the wireless client node. The client then requests the specific forms of authentication and encryption that it desires. Although the client and AP are already exchanging messages, the client has not yet been authenticated nor does it have an encryption key, and so several more steps will be required before the client can communicate with an arbitrary remote host over the wireless channel.
Mutual authentication and Master Key (MK) generation. Authentication takes place between the wireless client and the authentication server. In this phase, the access point acts essentially as a relay, forwarding messages between the client and the authentication server. The Extensible Authentication Protocol (EAP) [RFC 3748] defines the end-to-end message formats used in a simple request/response mode of interaction between the client and authentication server. As shown in Figure 8.32, EAP messages are encapsulated using EAPoL (EAP over LAN, [IEEE 802.1X]) and sent over the 802.11 wireless link. These EAP messages are then decapsulated at the access point, and then re-encapsulated using the RADIUS protocol for transmission over UDP/IP to the authentication server. While the RADIUS server and protocol [RFC 2865] are not required by the 802.11i protocol, they are de facto standard components for 802.11i. The recently standardized DIAMETER protocol [RFC 3588] is likely to replace RADIUS in the near future.

Figure 8.32 EAP is an end-to-end protocol. EAP messages are encapsulated using EAPoL over the wireless link between the client and the access point, and using RADIUS over UDP/IP between the access point and the authentication server
With EAP, the authentication server can choose one of a number of ways to perform authentication. While 802.11i does not mandate a particular authentication method, the EAP- TLS authentication scheme [RFC 5216] is often used. EAP-TLS uses public key techniques (including nonce encryption and message digests) similar to those we studied in Section 8.3 to allow the client and the authentication server to mutually authenticate each other, and to derive a Master Key (MK) that is known to both parties.
Pairwise Master Key (PMK) generation. The MK is a shared secret known only to the client and the authentication server, which they each use to generate a second key, the Pairwise Master Key (PMK). The authentication server then sends the PMK to the AP. This is where we wanted to be! The client and AP now have a shared key (recall that in WEP, the problem of key distribution was not addressed at all) and have mutually authenticated each other. They’re just about ready to get down to business.
Temporal Key (TK) generation. With the PMK, the wireless client and AP can now generate additional keys that will be used for communication. Of particular interest is the Temporal Key (TK), which will be used to perform the link-level encryption of data sent over the wireless link and to an arbitrary remote host.
802.11i provides several forms of encryption, including an AES-based encryption scheme and a strengthened version of WEP encryption.